TECHNOLOGY
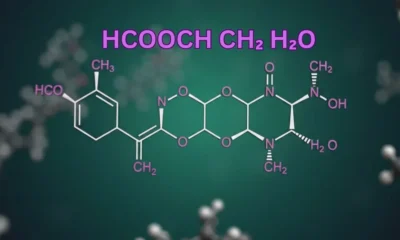
Insanony: The Ultimate Guide to Anonymous Instagram Story Viewing

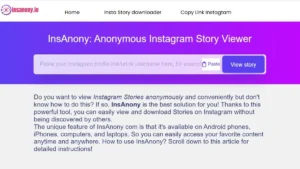
In an era when privacy is paramount, Insanony appears to be one of the few possible key solutions for Instagram users eager to view the profiles of others without leaving any traces of their activity. This unique application employs proxy servers to prepare the application so that nobody seems to perceive the identity of the people using it.
How Insanony Works?
Concept of Proxy Servers
At the heart of its functionality is the use of proxy servers. A proxy server acts as an intermediary between your device and the internet. When you use Insanony, your requests to view Instagram stories are routed through these proxy servers. This process masks your IP address and personal information, effectively hiding your identity from the profile you’re viewing.
Stealth Mode Functionality
Insanony operates in what is known as stealth mode. This mode ensures that your browsing activity remains invisible to the target profile. Unlike standard browsing, where your presence can be tracked through various means, stealth mode keeps your visit undetected, preserving your privacy.
Role as a Middleman
As a middleman, it processes your requests for Instagram stories without directly connecting to Instagram’s servers. Doing so prevents Instagram from recording your activity or linking it to your real identity. This approach maintains anonymity and reduces the risk of privacy breaches associated with direct browsing.
Security Measures
To safeguard user data, Insanony employs robust encryption protocols. Encryption converts your data into a secure format that is difficult to decipher without the appropriate key. This technology ensures that your browsing activity remains private and protected from potential cyber threats. Insanony utilizes secure login processes to prevent unauthorized access. This includes multi-factor authentication and secure password management. By incorporating these security measures, Insanony aims to protect your account from potential breaches and ensure a safe browsing experience.
Key Features of Insanony
- Privacy Protection: Privacy is a core focus. The application ensures that your identity remains confidential by using advanced proxy servers. This setup effectively hides your IP address and other personal details from the profiles you view, offering a layer of protection against unwanted exposure.
- User Control: This gives the user full control over their privacy settings, thus enabling them to have full control of their privacy. There are several options you can tweak according to your needs, such as choosing proxies you prefer, or they may hide proxies you don’t need. This level of control enables users to choose their browsing mode depending on their privacy level.
- Device Compatibility: It is also meant to support as many clients and platforms as possible. Regardless of the platform, mobile or otherwise, be it a smartphone, tablet, or computer, Insanony allows you flexible usability on the iOS, Android, and Windows platforms. The installation and the setup are rather simple, so the users can begin to explore the incognito mode without delay.

Benefits
Browsing Incognito
One of its primary strengths is its capacity to enable the user to anonymously read Instagram stories. This feature is especially ideal for people who intend to browse profiles of other users but do not want to be tracked online. It means that it would be possible for the users to navigate content without feeling like others are watching them or following them.
Enhanced Privacy
Insanony offers a significant enhancement to privacy compared to other browsing methods. By acting as a proxy and employing encryption, it provides a higher level of privacy protection. Users can enjoy a more secure browsing experience with reduced risk of data exposure.
Potential Concerns
Ethical Considerations
This is valuable for privacy protection, yet raises ethical concerns. The feature of browsing anonymously should be used with caution as it can be potentially used for stalking or any other malicious actions. The user therefore needs to consider the ethical factor involved in the use of such a tool and uphold high standards of decency when using it.
Privacy Risks
Despite its focus on privacy, using proxy servers does come with inherent risks. There is a potential for data interception or misuse if the proxy servers are compromised. Insanony takes steps to mitigate these risks through encryption and secure protocols, but users should remain aware of the potential vulnerabilities.
Future Developments
Insanony is continuously evolving, with plans for future updates and features. These may include enhanced privacy options, improved user interface elements, and expanded compatibility with additional devices. Staying informed about upcoming developments can help users make the most of the application. It values user feedback and incorporates it into its development process. By listening to user suggestions and addressing concerns, it aims to improve its service and meet the needs of its user base.
-

 BIOGRAPHY9 months ago
BIOGRAPHY9 months agoBehind the Scenes with Sandra Orlow: An Exclusive Interview
-

 HOME1 year ago
HOME1 year agoDiscovering Insights: A Deep Dive into the //vital-mag.net blog
-

 HOME1 year ago
HOME1 year agoSifangds in Action: Real-Life Applications and Success Stories
-

 BIOGRAPHY1 year ago
BIOGRAPHY1 year agoThe Woman Behind the Comedian: Meet Andrew Santino Wife